There are two types of governments in the world, Those that build complex surveillance software to spy on their citizens, and those that buy them–and our government is more the buying type.
Few nation-states have the budgets to build out complex surveillance software, but some are finding that ‘off the shelf’ software sold by dodgy companies are just as effective at a fraction of the price. The problem with buying of course, is that sometimes those dodgy companies that are manufacturing these spying software also sell their wares to repressive regimes like Sudan, and being on the same customer list with Sudan doesn’t quite bode well for any ‘moderate’ government.
Take Gamma Corp for example, the organization responsible for the FinSpy and Finfisher suite used by the Malaysian government in the run-up to the 2013 General elections. Another is Hacking team, an Italian based company that produces similar remote control software (RCS).
And in a bit of internet karma–both of these companies were hacked themselves…possibly by the same person.
In August 2014, Gamma was hacked and had 40GB of data forcefully exfiltrated from their servers. My analysis of that leak, revealed no information about Malaysian purchases of their FinSpy software simply because a large chunk of that data was encrypted.
Recently however, Hacking Team had a much more severe attack, one that managed to extract 10 times more data, and here I found ample evidence of Malaysian government agencies procuring spyware from Hacking Team presumably to be used against Malaysians.
The question of course is should you be worried, the answer is Yes, and not just for the obvious reasons. After combing though a trove of documents, I found that 3 government agencies procured the ‘flagship’ RCS software from Hacking team, and from my layman’s understanding of the law, none of them have authority to actually use it.
Worst still, some e-mails point to incompetent IT skills as well as bad Procurement practices, that actually annoyed hacking team’s salesforce. I will conclude this post with why this attack on Hacking Team has a positive outlook for regular internet users, and why our government agencies procuring this stuff isn’t exactly ALL THAT BAD.
What did the Government Buy?
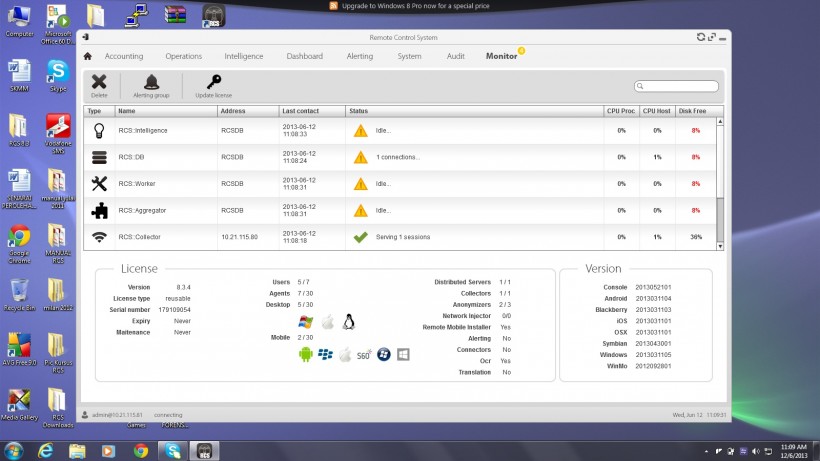
 But let’s start with the RCS software itself.
But let’s start with the RCS software itself.
What exactly was being purchased? Well according to the Hacking Team Brochure (you can download here)
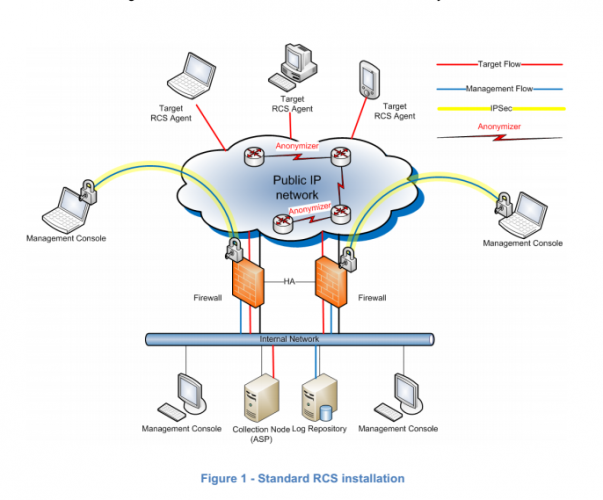
Remote Control System (RCS) is a solution designed to evade encryption by means of an agent directly installed on the device to monitor. Evidence collection on monitored devices is stealth and transmission of collected data from the device to the RCS server is encrypted and untraceable.
RCS installations are deployed at the Customer’s premises, thus guaranteeing to the
Customer total control on its operations and security.
In other words, RCS is a piece of spyware, that when installed on your computer or smartphone, begins monitoring your internet usage, surreptitiously transmitting that information back the Command and Control (C+C) servers for further manual investigation. This is a typical piece of surveillance software, no different from FinFisher and probably hundreds of other dodgy software sold worldwide, but make no mistake this is spyware, built to spy. And the last I checked, even Government agencies need to go through proper procedures and have sufficient oversight before they go spying on citizens.
The RCS still requires to be implanted onto your system, and for this Hacking Team utilized vulnerabilities in software like Microsoft Windows, Google Android and Adobe Flash that weren’t publicly known. Meaning they knew of weak spots in Flash that even the manufacturer wasn’t aware of, so that their RCS agent could be implanted onto a victims machine. These ‘0-day exploits’ (as in the Zero day) are rare, researchers spend years finding such things, and Hacking Team had quite a number of them, fortunately since this disclosure those vulnerabilities are being patched.
Which government departments?
 Buying surveillance software in itself isn’t wrong. After all, the police are well within their authority to purchase such software as part of their investigative powers.It’s not just acceptable, it’s actually expected that the Police ramp up their surveillance capabilities–phone taps and binoculars don’t get you enough information these days. I don’t oppose specific surveillance, where the police in their authority with proper judicial oversight run a ‘stake-out’ on criminal suspects. What I oppose is bulk surveillance, where the police without judicial oversight are given blank cheques to spy on whomever they choose. There’s a nuance that many don’t quite understand. Of course, all of this violates the Computer Crimes act, since the very act of using RCS is ‘hacking’, therefore these government agencies by just purchasing the software have admitted to hacking citizens. Wonder when any of these guys will be seeing the inside of a jail-cell.
Buying surveillance software in itself isn’t wrong. After all, the police are well within their authority to purchase such software as part of their investigative powers.It’s not just acceptable, it’s actually expected that the Police ramp up their surveillance capabilities–phone taps and binoculars don’t get you enough information these days. I don’t oppose specific surveillance, where the police in their authority with proper judicial oversight run a ‘stake-out’ on criminal suspects. What I oppose is bulk surveillance, where the police without judicial oversight are given blank cheques to spy on whomever they choose. There’s a nuance that many don’t quite understand. Of course, all of this violates the Computer Crimes act, since the very act of using RCS is ‘hacking’, therefore these government agencies by just purchasing the software have admitted to hacking citizens. Wonder when any of these guys will be seeing the inside of a jail-cell.
So which government departments purchased the software?
The ‘Government’ is a pretty abstract term that encompasses way too much, let me be specific, there is evidence of 3 specific government departments products from Hacking team. The MACC, the Prime Ministers Departments (wrongly refered to in the e-mails as PMO) and a Malaysian Intelligence body that goes by the name of MYMI.
Which begs the question, does the MACC, PMD or MYMI have authority to run surveillance programs? From my reading of our laws like POTA and SOSMA, the laws only allow the police to spy on citizens, and only police officers above the rank of superintendent can intercept internet communications without prior approval from the courts–no where in any of those acts does the law grant power to bodies like the MACC, and it certainly shouldn’t be granting power to the Prime Ministers Department. I could be wrong, but hopefully some lawyer reading this may correct my perception. Of course if MYMI was a police intelligence outfit, then obviously under the law they have the authority to operate such systems, but again, do they have the right to hack a computer system? Penal code says it’s wrong to kill someone, but a Police Officer in a gunfight is allowed to, are there such provisions in our legal framework to allow the Police to hack into computer systems?
The question on my mind is, if the Prime Ministers Department doesn’t have sufficient authority to run a surveillance program, why is it buying surveillance software? Someone without a gun license certainly shouldn’t be allowed to buy an M-16.Although we probably shouldn’t worry, because a report from Hacking stated that “they (PMO) are not competent to use deploy RCS on their own.”
There is a Cyber and Space security division within the department, but we’re not talking security here–these are weapons. The difference between security and offensive software is that one secures a server, while the other is meant to break them. Why would a ‘security’ division buy surveillance software. Don’t let the government throw you off with words like cyber and security, this has nothing to do with both, it’s purely an offensive application used to spy on people.
While the invoicing data confirms these 3 government departments, 3 others seemed to be in the process of procuring Hacking Team software. This includes a ‘taxation agency’ that had direct physical access to machines, Police Commercial crimes division and PKSB. PKSB, was describe by Miliserv as a very powerful outfit within PDRM, whose approval to procure Hacking Team software came from the IGP himself. But once again, I have no issue with the Police this software, although the Police should be aware, that the names and Passport numbers of 5 of their staff who took the training in Milan are up on the internet.(Names of the 3 staff from the Prime Ministers department are also online).
Also, why the hell is a tax agency buying spying software for? The answer lies in which tax agency gets 1.5% of all taxes collected. I certainly hope, the computer crimes act doesn’t allow the LHDN to hack computers.
You also might notice MCMC on the list of ‘potential customers’, but I didn’t find any e-mail in the stash to validate that.
Attibution
When we discover these RCS trojans in the wild, it’s usually very hard to attribute the attack to specific actor. We’re left to make guesses based on the victim and the way the victim was hacked.
For example, in 2013, we saw a similar attack based a on file entitled “
Remember the ‘Bangladeshi voter’ incident in 2013–well here we have evidence that the documents that went viral purportedly showing the Bangladeshis in our airport actually originated from the Government itself. Let me repeat that–the government was spreading the rumor of Bangladeshi voters, not just the opposition.Here is the wikileaks link in case you’re interested. So while the government is complaining of Social media used to spread rumours, they themselves are responsible for some of the negative publicity, presumably to get a gauge which citizens are forwarding the ‘planted’ rumours.
There was a similar document about the idelible ink issue, and one rather formal looking document from the MCMC to Felda that was implanted with this spyware. The plot really does get juicy.
Juicy, Juicy Details
Let’s get into the meat of the subject, all 3 department procured similar software, but all 3 had problems.
MACC and Prime Ministers Department procured theirs from a company called Miliserv Technologies, that operates out of Kota Kemuning Shah Alam.This is not a small company, they were incorporated in 2005 with RM1 million in paid capital, and manage to secure more than Rm8.4 million in contracts for Kementerian Dalam Negeri (on top of their sales of RCS).
Without going into details of the company, suffice to say they aren’t really up to spec in supporting a software of this complexity. The support staff had issues even troubleshooting a NAT problem, and in some e-mails asking rudimentary questions like “can this VPS support the anonymizer“, what really tickled me was the fact that this ‘secretive’ government surveillance program operated under the Cyber Security divison of the Prime Ministers department was running on a….UNIFI connection!!! Which is the equivalent of driving a top of the line Lamborghini on a kampung dirt road.I saw e-mails within Hacking Team complaining of the dynamic IP of Unifi, recommending Miliserv to switch to fixed IP broadband instead. Less funny was the fact that screenshots confirm that the machines used for this multi-millon dollar spying operation, wasn’t even running a genuine version of windows. [Microsoft, please take note]
The MACC servers were also the ones discovered by CitizenLab in their report at the end of 2014, and were promptly moved to different countries. What that means is that the MACC ran investigations on Malaysians (presumably), but had the data of that surveillance routed outside of Malaysia to Fort Lauderdale in the US, and the Ukraine, that’s not quite acceptable. The data transmission from an RCS installation might be encrypted, but I doubt the storage of that data is.
The big letdown for me was that the MACC and PM’s Department had Miliserv run their spying operations and not the agencies themselves, and in one case the server was hosted on Miliserv premises. This is problem, while the law may allow specific government agencies to run surveillance, it certainly doesn’t allow a 3rd-party contractor to do it–and we have here is Miliserv staff having access to private data of Malaysians.
MYMI on the other hand, procured their RCS through a secretive ‘K’. In some ways it’s quite smart to use a secret handle, thereby reducing the exposure you suffer when the other end of the e-mail suffers a catastrophic hack like this. In other ways, it’s not so smart to sell Millions or Ringgit worth of surveillance software to a Government department and do so while operating a e-mail address that ends with @hotmail.com. It’s even less smart to have missing dongles shipped to your home address attentioned to your real-name. I can’t link to that e-mail as it is personal information, but you know who you are ‘K’.Plus it seems strange that Malaysian intelligence was procuring surveillance software from a Hong Kong based company, when the same manufacturer of that software already has a local partner.Hacking Team were joking among themselves that they should start charging for the replacement dongles.
Then we have the typical perception that Malaysians have of their government. A couple of guys over at Cybersecurity Malaysia, thought the best way to forge a ‘strategic’ relationship with Hacking Team was to fly 5 members from Malaysia to Milan for a meeting–listen if you’re customer, the supplier comes to your office not the other way around. Also, the Malaysians for some reason weren’t happy with just going to the Hacking Teams office in Singapore, choosing Milan instead—this is software, you don’t need to see a factory, why do you need to go to Milan? Haih!
What I found annoying was that these guys were smart in encrypting the invoices, and sending the encryption keys via sms. That’s something we all can learn from this, whenever sending private information via e-mail, encrypt via WinZip and send the password in a separate channel.Or send a link, and then destroy that link once the data is received, that way you limit your exposure in time.
I’ve saved the best for last though. Miliserv Technologies, sent and e-mail to Hacking Team, claiming to be representing the Prime Ministers Office, inquiring about a “Network Injector Appliance (NIA) especially about how to deploy an agent at the ISP”. What the hell is the PMO requesting for spyware to be deployed at a Malaysian ISP for? Why do they need that?
What does this mean?
E-mail wasn’t the only thing leaked in this hack. Source code to the RCS and how it actually exploited operating systems like Android and Windows were also made available to the public. Because of that, software manufacturers like Adobe, Google and Microsoft rushed to publish patches that fixed the vulnerability–what that meant was that the exploits that Hacking Team relied on to install their backdoor RCS no longer exist, rendering their product obsolete and in some cases completely useless.
Some may argue this is bad, and surely it’s bad for Hacking Team, and probably bad for local law enforcement that rely on these tools. This is why regardless of whether MYMI was indeed the special branch or something else, the point is moot, because by the end of the month, this expensive software that our government procured wouldn’t be worth anything.
But here’s another take on it, we just patched a ton of exploits that we didn’t know about before, rendering applications like Flash, Android, Windows more secure than they were before the hack. Because we have to make the assumption that if a company like Hacking Team found these exploits, other companies, and certainly other well-funded government agencies probably knew about them as well, and we just closed yet another door for them to spy on the public.Maybe they have more doors, maybe they have only one, but the fact is, we work on securing software and this is a step in the right direction.
Who is Hacking Team to make those judgements anyway? Why should a corporation get to decide what governments get to use exploits and which don’t?
Conclusion
We’ve known all along that Governments buy surveillance software, and sometimes bend the laws to use them, this is just another confirmation of what we already strongly believed.
Post-Script: Can we trust the data?
I’ve said it before, e-mails aren’t good evidence, as any digital data can easily be replicated and forged to absolute perfection. But this isn’t just e-mail, this is more than 1 million e-mails and a couple hundred documents surrounding Malaysia, and collectively they make a much stronger case.
For example, all the e-mails appear consistent, both chronologically and factually. The e-mails from Miliserv come from people whose names match what we see in the SSM data for the company, the names also correlate to Malaysian IC numbers in the e-mail chains that match data on the SPR website for voter checklist. Some e-mails list staff of the various government departments going for training, and those names are actual employees of the agencies. Addresses given are actual Malaysian addresses and a lot of the context is set to something only Malaysians would know, like the name of the secretary of Cyber Defense in the PMO, or the fact that Malaysia has an IGP, and terms like Unifi are thrown around. I went in very deep in analyzing Malaysian e-mails, and this data breach involved many many countries, yet I couldn’t find a single piece of data that was inconsistent with the story.
Also, together with the e-mails were those prized 0-day exploits I mentioned. As more and more of those exploits are discovered, they’ll get patched, reducing the effectiveness of RCS. But because those exploits were also released, we can be fairly confident this is the real thing, you can’t forge those unless you’re sufficiently well funded, we’re talking around 50-100k USD per exploit.
So either this 400GB of data was forged through an intricate plan that involved probably thousands of people, or the data was hacked. As more data becomes available, and as more of the pieces fit together, it becomes more reasonable to assume that data was hacked rather than forged. Perhaps if Sarawak Report revealed all the e-mails they had, it would make a much stronger case.
Nice job in doing the reading/research. Enjoyed reading it.
Nice job in doing the reading/research. Enjoyed reading it.