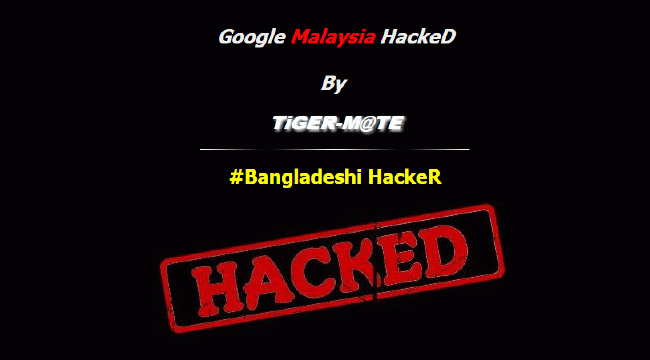
 Last week visitors browsing to Google’s Malaysia website were greeted with a big bold image stating the website was hacked. The media had a field day proudly proclaiming that Google’s website was hacked, because that was exactly what the page they visited said….Google Hacked!!
Last week visitors browsing to Google’s Malaysia website were greeted with a big bold image stating the website was hacked. The media had a field day proudly proclaiming that Google’s website was hacked, because that was exactly what the page they visited said….Google Hacked!!
Only, Google wasn’t hacked.
They’re the agency in charge of managing all internet addresses ending with the .my suffix. Hackers had infiltrated MyNic, and reconfigured the systems to point www.google.com.my to their own servers instead of Google’s. Then they simply pasted a silly looking screen that boldly proclaimed their ‘hack’ to the world, claiming to hack Google rather than MyNic—which is what you’d expect from hackers. But the media, took that to mean Google was comprimised, and boldly proclaimed that Google Malaysia was hacked, going so far as to ask if ‘user data was compromised’.
The analogy is that if someone hacked Waze, and took all unsuspecting tourist who were trying to get to KLCC, and re-directed their route to an abandoned warehouse in Klang, the headline for that story should read “Waze hacked” instead of “KLCC destroyed”. Everyone knows how absurd a headline like the latter would be, but very few people would think the same thing the moment ‘internet things’ get involved–if the website says Google hacked, surely it must be true, in the same way that if Waze says this dilapidated factory lot is KLCC, surely it is, because Waze is never wrong right?!
The problem of un-suspecting tourist
The problem is that most internet users are the equivalent of un-suspecting tourist in a foreign land, not knowing the geography or even the language of this country we call the internet. I’d wager 95% of internet users haven’t even heard of a Domain Name Server (DNS) let alone understand how it works, yet this fundamental piece of technology is what makes the world wide web possible. And by the way the internet and the world wide web are NOT the same thing?
That 95% isn’t some number plucked from the thin air , I have evidence to back this , my post on how to change your UniFi WiFi password gets about 150 hits everyday.But if I tweak the technical complexity a bit higher, like Port Forwarding your UniFi router, or implementing DDNS, that number drops from 150, to just 10 a day. That’s a factor of 15 difference, people who know things like DNS and want to do DDNS are outnumbered significantly by the clueless internet user.
I’d say 95% of Malaysian users wouldn’t know how to change their WiFi passwords without Googling, and if you need to Google just to do something that simple, you definitely don’t know how DNS works. (BTW, the title of the post UniFi WiFi is technically wrong, as the WiFi and UniFi connection are separate things, however, some SEO from Google told me that’s what users were searching for)
Too much technology, too little knowledge
We’re at a really bad place. Technology is so ubiquitous and pervasive, that even my mother now is on Facebook, Whatsapp and Viber, yet she has absolutely no idea how these things work, and just like your mother is clueless on how to secure herself from online threats, in this space that she frequently visits. Lots of technology, lots of people using it, but very few who do it securely.
Hence, I think geeks like me have a social obligation to help others, in the same way Doctors have an obligation to heal, or journalist have an obligation to report the truth, even when it hurts them, and even when they get little to no compensation for it, it’s a duty and responsibility.
And if we don’t step up, the consequences will be catastrophic.
Unfortunately, the geeks aren’t really helping. We’re either sequestered in their ivory towers, or hanging out on forums that no one but geeks visit–which leaves the rest of the ‘civilian’ population having to read their tech news from places like TheStar or RakyatPost, who may be able to report on politics and sports, but they’re definitely under-staffed and incapable of reporting on technology.
Mainstream media reporting of CyberSecurity
Take for instance yesterdays article in TheStar, titled “Cyber attack launched after MH370 went missing”, which on the face of it looks like a good attention grabbing title. But MH370 went missing a year ago, why are Kaspersky talking about this now? Sure they have their cybersecurity summit in KL this week, but that’s pretty stale news in the fast-moving world of computer security.
If you took the time to visit the Kaspersky blog (which is an amazing blog to follow), they detail the APT wars.What Kaspersky were reporting on their blog was that :
- Cyber-attacks were carried out by a group called Nakion, targeting senior diplomatic entities in ASEAN
- This group carried out attacks shortly after MH370 went missing
- THEN, a totally separate group called Hellsing, decided to attack Nakion back
- Hellsing replied back to the Nakion attack e-mails and tried to use social engineering and other techniques to determine the origin of Nakion
- Hellsing targets included Malaysian government entities as well as other ASEAN member states
- Kaspersky labled these the APT wars, because it was the first time they’ve seen an attacker being attacked back.
Now, if you go back to the original star report, you’ll find that it only reported (1) and (2), while the actual point of the story, that the attackers were being attacked, was missed out entirely. Either Kaspersky didn’t share this information in their summit (quite unlikely), or the reporter from TheStar went to the summit, heard the first few opening slides, and then dozed off the moment the Kaspersky folks talked about APTs and RATs… Advanced Persistent what now??!!
Or a third possibility that the reporter did report on the entire story, and the editor cropped out only what they thought was interesting to the Malaysian readers.
Doesn’t matter why it happened, the fact is most Malaysians didn’t get to read the full story. The only Malaysians who would have even had a chance to gaze upon it would be the tech-geeks themselves who subscribe to the Kaspersky blog or other cyber security news outlets, but how many of your mothers are reading security news every week?
The conclusion I draw is that if you rely on TheStar or RakyatPost for your tech news, you’re going to be either mis-informed (like Google hacked) or un-informed (like APT wars).
How can we fix this?
So what’s a tech geek like yours truly to do? I don’t have the media muscle of people like the star, this blog barely crosses 30,000 hits a month, I’m a nobody.
But if I were wave my magic wand and get the mainstream media to buck up and report on tech news accurately and comprehensively, would people even understand what was going on? How do I explain the Google Hack without first explaining DNS, and how would you even begin to talk about APTs, let alone Hellsing vs. Nokian? These are not trivial to understand, but their vital.
This is real challenge facing geeks, how do you make these cyber security topics relevant to the public, to get them interested and informed? Fortunately, there is a role-model to follow.
Be the Neil DeGrasse Tyson of Tech
Enter Neil DeGrasse Tyson, he’s the guy who hosted the Cosmos series, and if you just Google his name, and listen to his lectures, you can sit for hours through his narration, while he astounds you on topics like black holes and death comets, stars and planets. The moment he speaks, audiences just falls in the palm of his hand, but he’s talking about physics, and science, and the last time I checked the public wasn’t all that interested in those subjects, how come their interested why Dr. Tyson speaks?
How does he get people interested in topics, that they generally don’t care about? What can the cyber security folks do, to follow in those footsteps?
I don’t have a full idea, but here’s some key takeaways.
First step, stop using the freaking acronyms. In astrophysics, things are given easy to understand names.
Universe starts with a big release of energy–Big Bang.
Dead star that sucks everything with its enourmous gravity–Black Hole.
Unknown mass in the universe that we can’t see–Dark Matter.
The names make perfect sense, now contrast that with Advanced Persistent Threat of Domain Name Server. If we’re really serious about communicating with the public, we need to keep this jargon in the IETF and IEEE documents, but away from the public. We need easier names to explain to the public.
Advance Persistent Threat—Bad Ass Hackers.
Domain Name Server–Web Address listing.
Next we need to stop feeling the need to go to the nth-degree to explain everything. No one has time for a 1500 word document explaining how this Bad Ass Hacker broke into a server, we need to compress it into 300 words, it’s not impossible, we just need to prioritize and distil the message…every single time.
Finally, we need to get off our high horses. Dr. Tyson doesn’t laugh at people who don’t know that light is made out of photons, in fact he seems to get a kick from teaching. Cyber-security ‘professionals’ usually get a kick from feeling superior and mighty. I admit, I do this sometimes, when I arrogantly tell people to use better passwords, rather than take the time to explain why they need to protect their phone.
I guess at least acknowledging that there is this enormous understanding gap in the general public, and how the geeks aren’t really doing anything about it, is the first step towards actually fixing the situation.