I’m a big fan of the D-Link DIR 615 router, I think Telekom Malaysia made a pretty good choice selecting it as the default router for Unifi accounts. To be fair, TM have made some bad choices as well, but we won’t go into that here, overall the router isn’t top notch, but it gets the job done.
Unfortunately, D-Link as a company has come under the spotlight for some rather funky security practices. First, there was a rather questionable backdoor that D-Link installed on a couple of older versions of their routers, the router basically granted anyone access to D-Link routers by just changing the user agent string of their browser–worse still the back door carried the name of the author….it was Joel.
Fortunately, for Malaysians, the backdoor didn’t affect Unifi routers–as far as I could tell anyway, and D-Link have since fixed the issue.
Just last week, though a rather obscure post on bugtraq, which was then quickly re-posted to a couple other forums, detailed a more intrusive exploit, one that Unifi Dlink routers were susceptible to. This one, didn’t grant you access, but it would grant you the username and passwords of all users of the routers–literally giving you the keys to the gates of your router. As far as I can tell–this impacts EVERY D-Link Unifi router there is.
The hack is so simple, it requires no additional tools other your browser and quick copy-n-paste. All the attacker is required to do is to enter the following url:
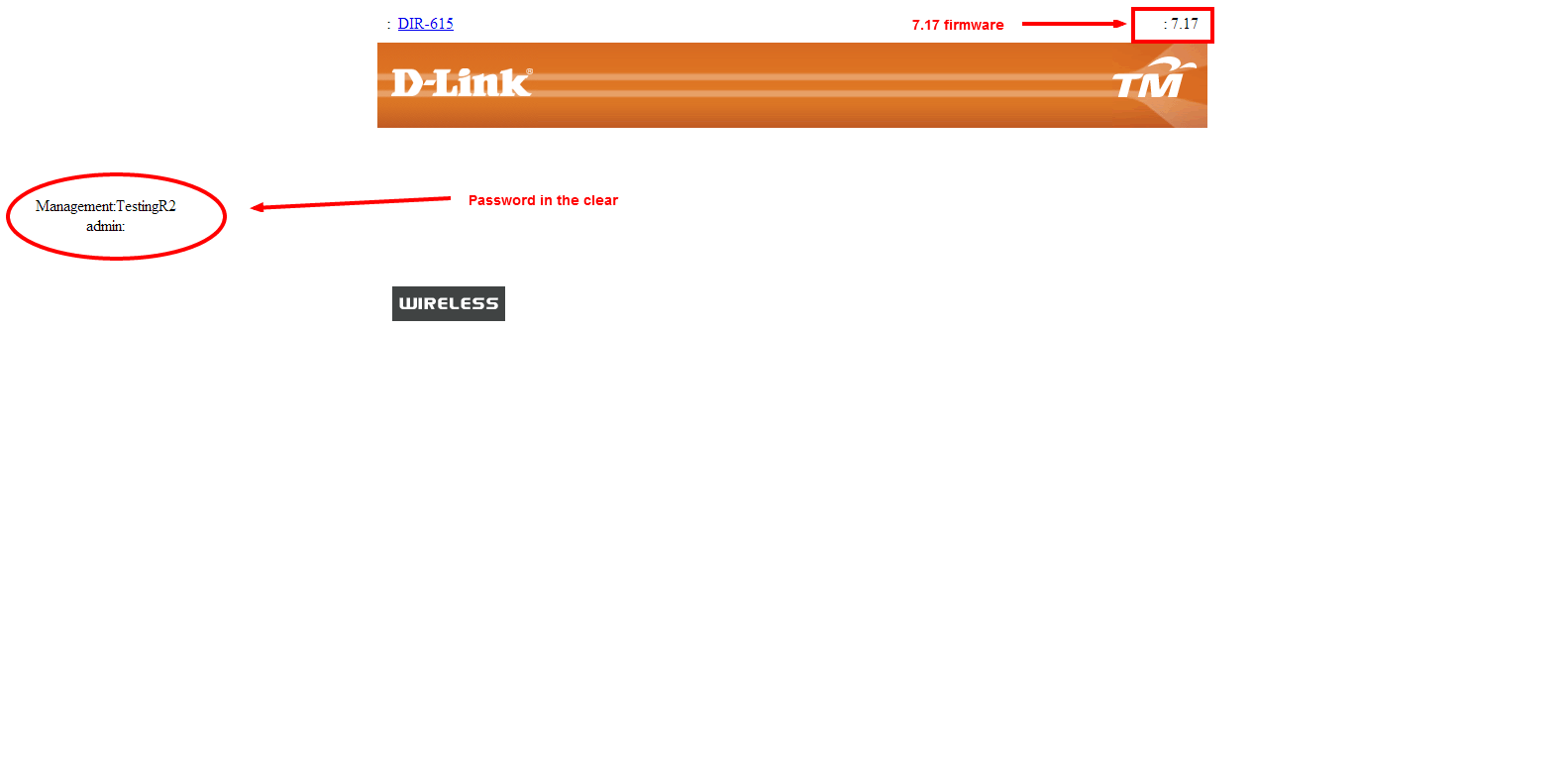
http://XXXXX:YYYY/model/__show_info.php?REQUIRE_FILE=/var/etc/httpasswd
Where XXXXX is the router IP address, and YYYY is the port on which it’s operating on. Then the router will miraculously display it’s security credentials to you, and you’re good to go. Using Shodan, I’ve verified that this works with nearly every firmware (pictures are blurry, click to open the full image)
D-Link have yet to release a patch for this, and the guy that published the bug didn’t really follow the rules. Usually D-Link should be alerted of such a bug and given time to fix it before the vulnerability is published.
However, since literally hundreds of thousands of Malaysian households are now susceptible to this attack, you need to know. More importantly, there’s nothing you can do about it with your current router firmware. No counter-measure is possible, it’s like living in a house where the door won’t lock, or the gate won’t close–how will you sleep at night?
Don’t despair you have two options to fix this:
1. Upgrade your router firmware to DD-WRT, Unfortunately, the guys over at Unifi Athena have been on a really long hiatus–and all the websites you search for information on this refer to them. Hopefully I’ll have time to publish a tutorial on that soon.
2. Change your router to a new Asus/Tp-Link router. I personally use the N12, but any of the Unifi compatible routers work pretty much out of the box.
3. That may fix the short-term though, in the long run, you’ll need to pay attention to security practices and upgrade your router firmware accordingly–provided the manufacturer actually releases patches. It’s inconvenient, but security requires effort.

You can also ssh to this router.
1. Get the username and password of your router from this blog.
2. On Linux/Mac/FreeBSD computer execute below command
ssh [email protected]
3. Type password when prompted.
4. Now you are inside the router’s “sh” shell.
Let me see how to
1. see all partitions
2. back up using the command “dd”
3. find files relevant to HyppTV
This helps to configure HyppTV after flashing DD-WRT.
This SSH was working on F/W Ver.: 7.09B
Interesting, thanks for the comment man 🙂
I think it would work on windows machines as well, just have to setup an SSH client like putty. But good comment, I’ll see if I have time next week to experiment.
I’ve two routers with one DD-WRT and another as given by TM. Let me see what the original config it has and patch DD-WRT.
Okay, finally learnt that WAN2 connection links to LAN4 according to port mapping.
By this time I’d got idea it is somewhere bridged. Command brctl helped me figure that out.
Also someone has laid foundation of using internet and IP TV using OpenWRT http://blog.namran.net/2012/08/05/setting-up-openwrt-to-work-with-tm-unifi/
Will check it tonight.
any solution to unlock the router that didnt supported by unifi ?