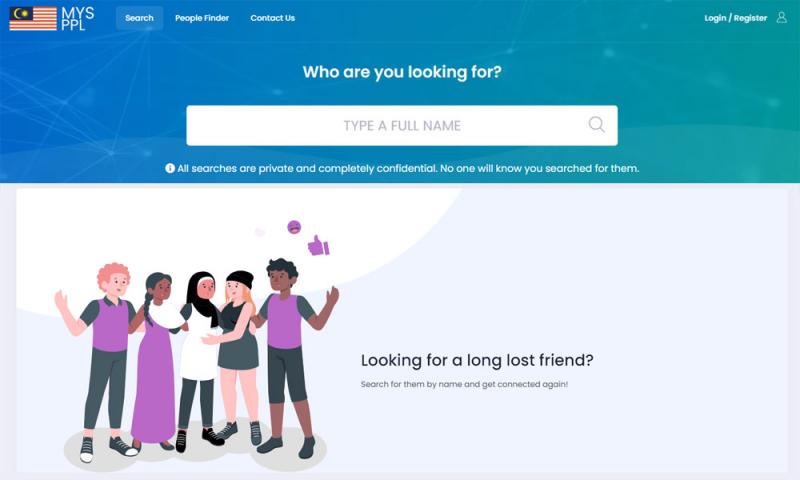
On September 2021, malaysiakini reported on a website called mysppl, that was selling personal data online. The site used previous breached data on Malaysians, and was selling it to anyone with a credit card (or Grabpay account).
Note to aspiring criminals.. the last thing you want when doing something illegal like selling personal data ,is to tie that back to Bank Account by accepting payments. But I guess, anything goes these days.
Anyway…
I decided to see whether I could use generic Open Source Intelligence (OSINT) techniques to try to find out who is behind the site, and this post is about my journey through that process.
Let’s go…
First, I did a regular WHOIS lookup on the domain. Most registrars offer free domain anonymization these days, but this is still the first port of call you want to try. Alas, no luck here, as the domain has the WHOIS data anonymized.
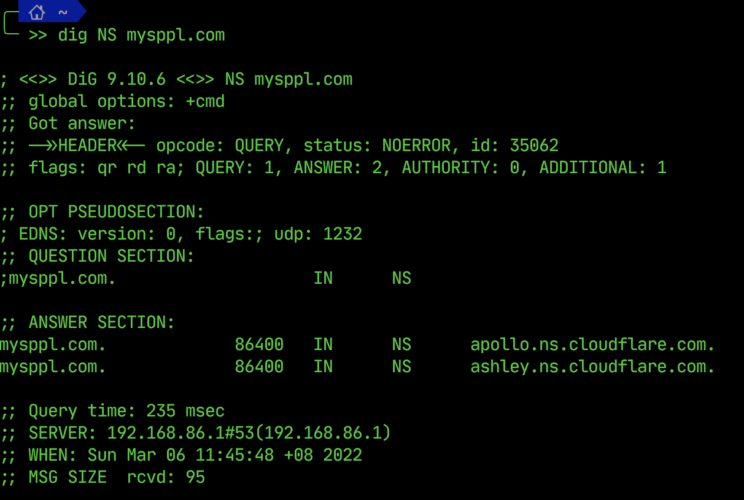
OK, no big deal, I was expecting it to be that easy. Now, let’s try to figure how where this website is hosted. Again, most websites now sit behind a CDN, which makes OSINT more difficult, but it’s still a mandatory step to at least try this. Running a dig NS <domain_name> command will give us the Nameservers used to host this — and here we see it’s hosted on Cloudflare 🙁
Next, I ran a ShodanHQ search and it turned out blank as well. Haih!.
But let’s keep chugging — on to Cert Transparency logs. Using crt.sh, and searching for mysppl.com reveals some rather interesting tid-bits.
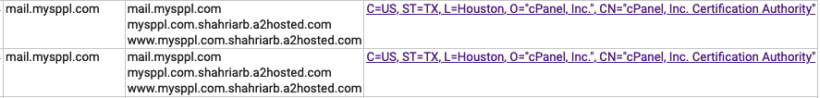
Oooh — this looks interesting. A2hosted is a hosting provider — but what does Shariarb mean? Let’s dig further. If I search for Shahriarb.a2hosted.com on crt.sh, I get even more weird domains:
At least we have a bunch of domains to search. I’ll spare you the details of the random domains that seem to be hosted here, but want to highlight two interesting ones:
The first is an insurance company — that has a bird logo on it:

And the second is a automotive part and supply website, take note of the phone number it’ll come in handy later:
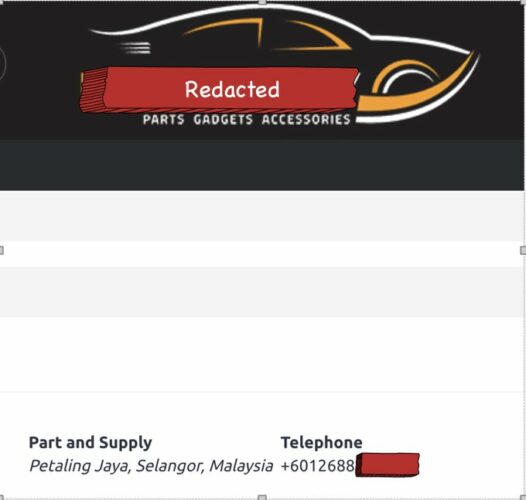
OK, after diving through those various domains, I decide to do WHOIS History searches on these domains. I registered for a free account at WHOISXML, and ran a few queries. These are recorded WHOIS historical data, and after searching through some of domains I found this:
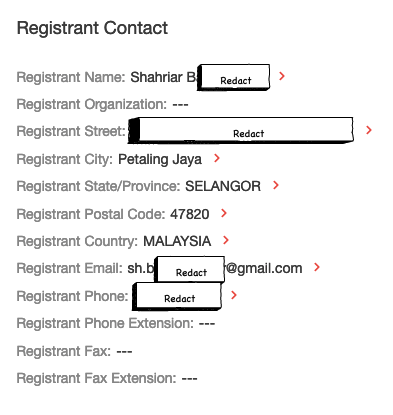
Finally a Shahriar B — it’s a name!
If we do a quick search for the domain, we end up with a LinkedIN profile of the CTO of the insurance company with the bird logo:
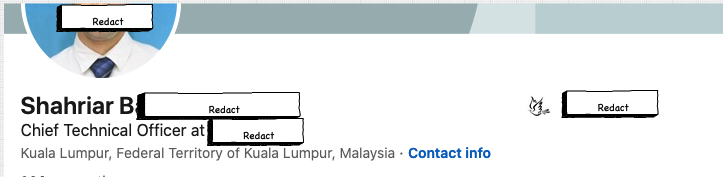
Now if we reverse search the WHOIS data for his name, we find other domains, including one with a phone number that’s just 1 digit off, from the phone number of the auto-part supply website:
I think there’s enough to conclusive prove that Mr. Shahriar B ran mysppl.com for a while. And after I started poking around he decided to shut down the website. Profiting off data breaches really isn’t cool man….don’t do it.
Fortunately, mysspl.com is now shut for business, let’s hope it stays that way.