 The team over at the FireEye threat intelligence published a special report(pdf) detailing an long running (and still on-going) cyber-espionage operation that has targeted multiple entities in ASEAN countries, including Malaysia. The program was reported to be running for more than a decade, and the sustained period coupled with the list of targets the program had, led FireEye to believe it to be a state-sponsored activity, as no other other type of organization would be able to afford such a professionally run program, operated for such a long period of time with no discernible source of income.
The team over at the FireEye threat intelligence published a special report(pdf) detailing an long running (and still on-going) cyber-espionage operation that has targeted multiple entities in ASEAN countries, including Malaysia. The program was reported to be running for more than a decade, and the sustained period coupled with the list of targets the program had, led FireEye to believe it to be a state-sponsored activity, as no other other type of organization would be able to afford such a professionally run program, operated for such a long period of time with no discernible source of income.
The group were nicknamed APT30, an abbreviation for Advanced Persistent Threat number 30 (I’m guessing the 30 part, because FireEye have other APTs on their github page). APT is a cyber-security term coined to identify an attacker that has both the capability and persistence to target specific entities up until they eventually break, and then continue to suck information from their victims for a significant amount of time. Basically there are script kiddies, hackers and then the ‘Advanced Persistent Threats’, APTs are a class above the rest.
APT30 operated a suite of tools including back-doors, and command and control software that were given catchy names like Backspace, NetEagle, Flashflood and ShipShape. The tools demonstrated a fair amount of sophistication in the way the functioned, but what really impressed the FireEye team was the level of professionalism that the coders exhibited, the malware had a well defined version control system, automated tools to manage many of the operational task and even the functionality that allowed for the system to be operated 24/7 by a team working on shifts, with one window requesting the operator to enter their ‘attendant code’. I wouldn’t be surprised if the system even calculated yearly increments, and provided KPI reports in the background.
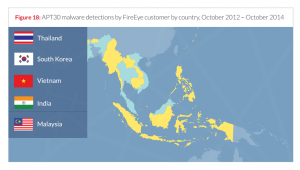
This isn’t some rift-raft put together from wannabe ISIS hackers attacking already vulnerable websites, this is a professionally run team, operating sophisticated malware, aimed at key diplomatic targets. The report claims that the developers of the code exhibited “carefully managed versioning systems and a consistent method for checking version information, performing updates, and ensuring only a single copy of a given tool is running on a victim host at any time”. I know of multi-million dollar software vendors that don’t exhibit that level of control over their software versions.
Fortunately, this well executed version control also allowed the team at FireEye to identify different versions of the software and the dates of their releases, then they tied those dates to various events in ASEAN, from 2011 ASEAN Summit in Jakarta, all the way to ASEAN-India Commemorative Summit in New Delhi a year later. These diplomatic events, which usually involve high level talks, correlate nicely to new releases of the malware that are too close to be coincidence. It would seem the APT30 group always shipped the latest and greatest versions just before the summits to ensure they siphoned off as much information as they could.
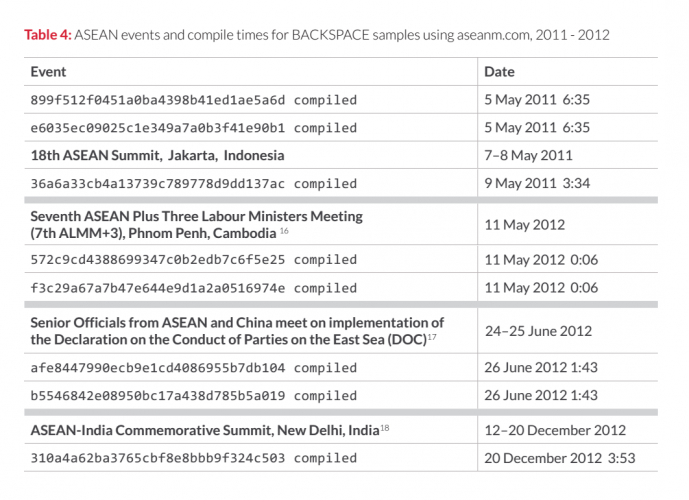
And if the list of targets, and the dates of new releases were not enough to convince you, the final ‘nail in the coffin’ was the way in which the infections took place. FireEye released a list of ‘decoy documents’, which were documents used in phishing e-mails to infect users, once the users opened the decoys, the malware would deploy and the machined would be owned. Decoy documents are usually a great way to determine the target group of an attack, malware targeting football players are going to have different decoy than if it were targeting banking officials, decoy documents for French speaking victims should be written in French, and so on.
In the case of APT30, 4 decoy documents were published in the report, but the one that caught my attention was titled “Report on China’s border security situation” that focused on territorial disputes between China and some of its neighbouring countries, and how that affected the security situation in the region.
Gee…I wonder who has a territorial dispute with China? (hint: it begins with ‘M’ and ends with ‘alaysia’)
Put that together with the fact, that the software has Mandarin all over it seems to lead to only one conclusion:
This was a sophisticated decade old Chinese state-sponsored operation that targeted officials in ASEAN and East Asian countries and was used to gather information from people close to issues such as Territorial disputers, boundary talks and Indian defense purchases.
Is this ‘shocking’?
No.
If you think that this sort of espionage is new, or that this represents a higher level of spying, you need to think again.
Think about the fastest plane mankind has ever built, the Sr-71 blackbird, built by the CIA to spy on the Soviet Union and its satellite states. The desire to spy on Soviet missile installations was so great that the CIA built a plane capable of flying 3.3 times the speed of sound, at an altitude 3 times higher than the peak of Mt. Everest—all in the good ol’ days of 1966!! You read that right, the fastest plane ever built came into production when England last won the world cup, that’s REALLLY long ago.
If you think this new piece of malware from China is ‘sophisticated spying’, what the hell do you call the Blackbird?
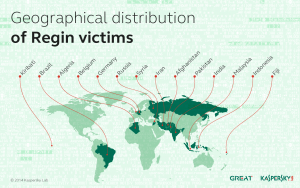
And even if we confine ourselves to digital spyware, APT30 still isn’t the most sophisticated attacker we’ve seen. Last year Kaspersky and Symantec independently discovered Regin, another state-sponsored piece of malware that exhibited such a high degree of sophistication, Symantec called it ‘groundbreaking’ and ‘peerless’. And unlike APT30, Regin has been attributed to the NSA and the GCHQ, agencies of Western countries that are certainly not aligned to China. Even then , Malaysia was one of the countries targeted by this peerless malware. I really wonder what kind of secrets we have that both the Chinese AND the Americans would spy on us.
“In the world of malware threats, only a few rare examples can truly be considered groundbreaking and almost peerless,What we have seen in Regin is just such a class of malware.”
-Symantec
The surprising thing about the APT30 revelations though is their targets, FireEye rightly claim that organization in Asia feel they won’t be targeted by such advanced threats, but as this report clearly demonstrates groups like APT30 are successfully exploiting that complacency.
FireEye go on to claim that 37% of their customers in Asia Pacific have detected advanced cyber attacks like those carried out by APT 30, which was above the global average of 27%. I’m actually quite shocked that the global average represents a quarter of their customers, while more than a third of their customers in APAC were attacked, that’s pretty good odds that government linked companies may have been attacked already.
I’ve been following cyber security news for some time now, but this piece really hits home because Malaysia was featured prominently as a targeted country (more prominently that the side note we got for Regin), and the level of sophistication and dedication the APT30 team demonstrated.
Conclusion
The one thing I must commend FireEye on is their use of the correct term Cyber-Espionage, instead of the more maligned term Cyber-attack. This isn’t an attack, this is good ol’ fashion spying, and it’s been around for ages, just that now we have the ability to attack from a distance, replacing spies like James Bond to anonymous geeks that sit behind computer screens and punch in attendant codes for their shifts.
No one starts a war because they found a spy. The Soviets knew about the Blackbird and the U2, they could even spot the planes on radar, and the Libyans once tried to shoot it down. These were mortal enemies locked in cold-war conflict, and everybody knew the other was spying just as much as them.
So no one is going to start a war just because we discovered things like APT30, or Regin, some might be angry or surprised, but this is just a digital version of something that’s been around for centuries.
To think, that a country like China with so much a stake in the South China Sea, and its enormous technical capability would sit back and not spy on Malaysia is preposterous, and doesn’t fit into any model of super-power the world has historically seen. There hasn’t been a single super-power nation state that didn’t have an intelligence agency that was interested in the dealings of its neighbours and allies, and what exactly do you think these intelligence agencies do other than spying?
We have to assume that we’ve already been infiltrated, the question is what do they know and how much do we tell them?
The Geek in me though, just loves reading how sophisticated these attacks have become, and believe me folks, I have a feeling we ain’t seen nothing yet.
i got the fireeye report but haven’t gone through it yet but as far as the secrets that i can think of is MH370 as well as high profile politician scandals like a certain Mongolian character. Since it’s an espionage, i think they’re just dumping & sorting data to get leverage when the time comes.
This was 10 years in the making, I don’t like to speculate about MH370 since the decoy documents don’t point to aviation or transportation authorities. Instead it points to border maritime disputes we have with China.