So I was wondering if I should publish this, but I guess I have to. If you’re one of the 500,000 Unifi subscribers in Malaysia, you need to know that your stock router–is completely hackable. TM has left you literally hanging by your coat-tails with a router that can be hacked as easily as pasting a link. So I was struggling to figure out if I really should have made this post, but in the end I think it’s better for you (and everyone else) to know just how easy it is to Hack Unifi accounts–not so you can hack them, but so that you can take some precautions over the situation.
But first, some caveats–everything I’m showing here is already public knowledge, the only difference is that I’ve culled and aggregated knowledge from different streams to show you just how easy an attacker can circumvent your password protection on your Unifi Dlink DIR-615 router, which is the stock router that comes with Unifi. It’s better for you to know about it than to remain oblivious to possibility that anyone from anywhere in the world, sitting in their room with their pyjamas on, can log onto to your router and start doing some rather nasty stuff.
Second caveat, is that as a result of this, some ‘kiddy-hackers’ may see this post and now be empowered with the means to attack, that’s a risk I’m willing to take to allow for everyone to know about it, so that they can do something about it. Keeping everyone in the dark about vulnerabilities of their routers is not a good thing. Security works better when everyone has access to the same information, this is how security works, and if you don’t agree–well tough luck.
With that said, here’s how you use Shodan, and a well known exploit to hack Unifi. The final exploit which doesn’t require any knowledge of the passwords starts at 4:08
Update 22-Jun: My Apologies: YouTube have removed my video because someone reported it as being inappropriate. I am appealing..I’m not sure what about the video was inappropriate, and I have made no attempt to mis-lead anyone. Stay tuned. I’ve updated the video with a Vimeo upload instead.
Hacking Unifi Dlink routers using Shodan from Keith Rozario on Vimeo.
Details of the hack:
1. To access the password page the appendage is /model/__show_info.php?REQUIRE_FILE=/var/etc/httpasswd
2. To search for Dlink Routers on Shodan the query is Mathopd/1.5p6 country:MY
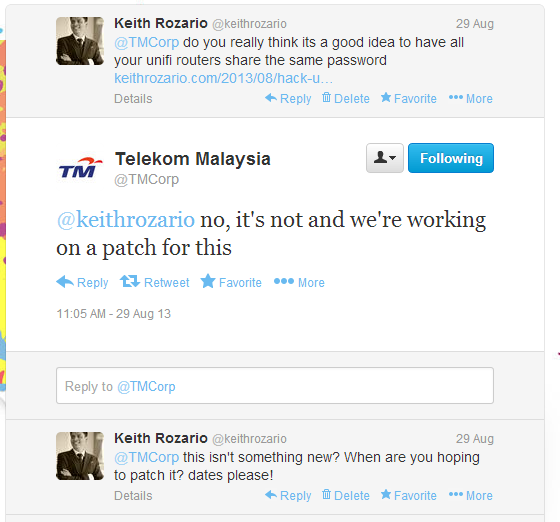
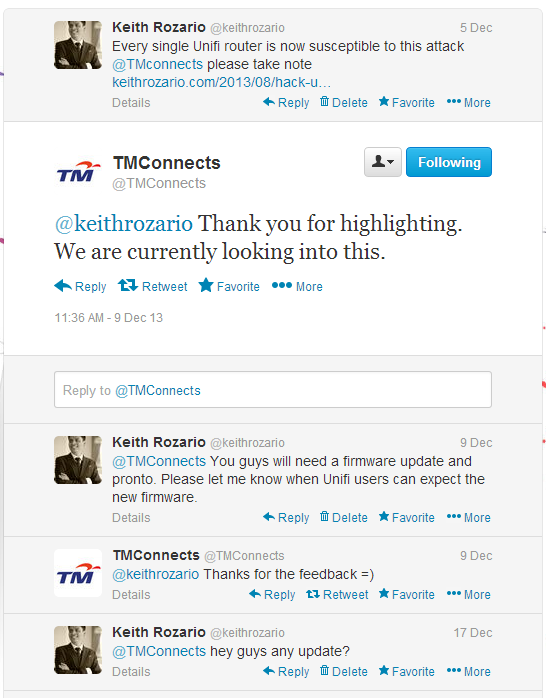
I’ve alerted TM to this much earlier, in August 2013 actually, and they promised they’d fix it by the end of the year. To be honest though, I don’t blame them, your router security is your responsibility and not TMs, so I think that TM isn’t doing anything wrong by not doing anything. A user should be responsible for the security of the router, just like how you are responsible for the security of your phone–even if you did get it free from Maxis or Digi. So anyhow, in the absence of any clear action from TM, I’ve taken it upon myself to inform you of the router vulnerability, and here’s hoping you do something to fix it.
As always–stay secure.
To address the issue check out my post on how to prevent this on your Unifi router, click on my post here.
So basically there’s nothing much I can do with this current router other than to replace it with another one right?
Stay Tuned Hiew–I’m working with someone who says he has a solution.
The router that came with streamyx have same vulnerability or not? I check the streamyx have different account in the router not same with the unifi and also streamyx use different type of model of router
Hey Lololo,
Most routers have some sort of vulnerability, so depending on which router you use you could be susceptible to an attack. The thing about streamyx, at least back in the day, was that StreamyX only supplied a modem, not a router so this exploit wouldn’t even work as modems don’t have IP addresses assigned to them–those belong to the computer connected to the modem.
https://www.facebook.com/photo.php?fbid=726635640683047&set=a.384496584896956.98126.384039804942634&type=1&theater
If we switch off remote management like Hanief said, so they can’t access my router by web, right?
but someone connected to the router using wifi or LAN cable can still use this. remote management is only for managing the router when you are not in range of the routers wifi signals nor connected via LAN cable. thats why i use a TP-Link TL-WR1043ND. i can allow only specific devices to access anything in the router, regardless if they have the username and password for the router
That’s correct–devices connected to your LAN via the WiFi can perform the hack. Especially true for businesses like restaurants that offer free WiFi over their Unifi Connection via the Dlink router.
glad you shared this even though im on streamyx not unifi so i can tell my friends and family.is this bug only on unifi?how bout streamyx stock modems?
StreamyX users have a whole range of routers–but every router has a weakness. You need to look at your specific router, and check if indeed there are published exploits for it.
Basically all you need to do to fix this is to change your router’s login password lol
do u read the comment below the video??
To access the password page the appendage is /model/__show_info.php?REQUIRE_FILE=/var/etc/httpasswd
all password can be seen, no matter what u change.
Wonder, how long using a published vulnerability on an old router counts as hacking and not bragging though…
Yeap, this isn’t hacking–but putting it in the title helps get peoples attention. It’s more a case of creating awareness really.
I disable remote access along time ago, but Is this dlink’s security problem for allowing router to read file from root? and why is the management account not in md5 hash while the admin one is hashed. anyway unable to block the file from readable from the php file, if you are running business and had given any guest password to your cutomer, the file are exposed.
Yeap. Exactly right.
[…] my method of ‘hacking’ the Unifi modems has a ridiculously simple work-around. Unfortunately, when I published the findings I was […]
Thanks Kar2on for sharing this finding. I’m a Unifi user with DIR-615 revision G2, it is very scary that I have affected to the password page exploit for more than 2 years without knowing it.. I have flashed my router to DD-WRT as I found out that there is no way for me to turn off remote access ( at least I cannot find it). I also written down my steps, if anyone interest can have a look. http://cakegiyh.blogspot.com/2014/01/flash-unifi-router-dir-615-g2-to-dd-wrt.html
change ur port number for remote access is alternative option to prevent the attempts
Nope. Shodan does a full port scan on all available ports.
Use Mikrotik, win at life 🙂
does the /model/__show_info.php?REQUIRE_FILE=/var/etc/httpasswd work on any other model besides the DLink 1?
Nope only Dlink–but not just the DIR-615, a lot of routers from dlink have this vulnerability
i use the same router and still with Mathopd/1.5p6, and i try to access from outside but not working.
for non-IT technical users, this will definitely be high risk.
Check this xiaopan.co
They have forum in chinese and malay too. I have no IT background. But i tried it on my unifi and its really do crack password in 3hrs for 8 digits WPA2. WEP just in couple minutes. Now for my own safety, i keep changing password once a week and use long characters as i can. Wifi also can detect from 2-10km away!! They discus all hacking strategy in that forum. Its our responsibility to keep safe our own network. I’am one of the victims before this and i figure out how to crack.
for me all d-link can be hacked not only 615 but all
Hi BingBang,
Not really. Not all D-Link routers use the same firmware, so not all are susceptible to the flaw.
[…] essentially made security research illegal in this country, so no one could test the security of Unifi Routers or WiMax access points without at least being worried of legal action.This provides legal […]
[…] Some suspected that Lizard Squad were running this large DDOS attack using nothing more than home routers–similar to the ones that UniFi provides and that I demonstrated could be hacked trivially over an internet connection. […]
[…] How I hack 4 Unifi accounts in under 5 minutes – How easy it is to hack Unifi accounts, and why you should change your router or firmware as soon as possible… […]
I don’t think you can access UniFi router from outside, It used to be able to, unless if the account is fix IP, but dynamic IP UniFi? Correct me if im wrong. I mean, you can search the device, but you can’t logged into it.
hi Nurashid,
Yes you can. Fixed IP packages allocated the same IP to you everytime you connect, while dynamic IP packages give you different IPs when you connect.
But from an external view, IPs are all the same, regardless of whether they belong to fix IP packages or dynamic IP packages.
Regards,
Keith
A sad day when the best way to protect your network is with a configurable router that is well configured. At one time, even google appeared on my blacklist and you still still find all consumer routers still vulnerable to the pineapple hak and similar hacks when there are cisco tutorials more than a decade old that describe how to configure a cisco switch to protect against this, unfortunately it requires configurable hardware.
Great , Hw to hack my neighbour password? :/
hello boss,
need your help. I just moved home. a new home already has a fiber optic cable unifi, I can continue to plug in to the modem. I do not know for setting to connect the internet. can you teach me for the setting ?
So basically there’s nothing much I can do with this current router other than to replace it with another one right?
Stay Tuned Hiew–I’m working with someone who says he has a solution.
The router that came with streamyx have same vulnerability or not? I check the streamyx have different account in the router not same with the unifi and also streamyx use different type of model of router
Hey Lololo,
Most routers have some sort of vulnerability, so depending on which router you use you could be susceptible to an attack. The thing about streamyx, at least back in the day, was that StreamyX only supplied a modem, not a router so this exploit wouldn’t even work as modems don’t have IP addresses assigned to them–those belong to the computer connected to the modem.
https://www.facebook.com/photo.php?fbid=726635640683047&set=a.384496584896956.98126.384039804942634&type=1&theater
If we switch off remote management like Hanief said, so they can’t access my router by web, right?
but someone connected to the router using wifi or LAN cable can still use this. remote management is only for managing the router when you are not in range of the routers wifi signals nor connected via LAN cable. thats why i use a TP-Link TL-WR1043ND. i can allow only specific devices to access anything in the router, regardless if they have the username and password for the router
That’s correct–devices connected to your LAN via the WiFi can perform the hack. Especially true for businesses like restaurants that offer free WiFi over their Unifi Connection via the Dlink router.
Wonder, how long using a published vulnerability on an old router counts as hacking and not bragging though…
Yeap, this isn’t hacking–but putting it in the title helps get peoples attention. It’s more a case of creating awareness really.
I disable remote access along time ago, but Is this dlink’s security problem for allowing router to read file from root? and why is the management account not in md5 hash while the admin one is hashed. anyway unable to block the file from readable from the php file, if you are running business and had given any guest password to your cutomer, the file are exposed.
Yeap. Exactly right.
Basically all you need to do to fix this is to change your router’s login password lol
do u read the comment below the video??
To access the password page the appendage is /model/__show_info.php?REQUIRE_FILE=/var/etc/httpasswd
all password can be seen, no matter what u change.
Use Mikrotik, win at life 🙂
glad you shared this even though im on streamyx not unifi so i can tell my friends and family.is this bug only on unifi?how bout streamyx stock modems?
StreamyX users have a whole range of routers–but every router has a weakness. You need to look at your specific router, and check if indeed there are published exploits for it.
change ur port number for remote access is alternative option to prevent the attempts
Nope. Shodan does a full port scan on all available ports.
for non-IT technical users, this will definitely be high risk.
A sad day when the best way to protect your network is with a configurable router that is well configured. At one time, even google appeared on my blacklist and you still still find all consumer routers still vulnerable to the pineapple hak and similar hacks when there are cisco tutorials more than a decade old that describe how to configure a cisco switch to protect against this, unfortunately it requires configurable hardware.
hello boss,
need your help. I just moved home. a new home already has a fiber optic cable unifi, I can continue to plug in to the modem. I do not know for setting to connect the internet. can you teach me for the setting ?
I don’t think you can access UniFi router from outside, It used to be able to, unless if the account is fix IP, but dynamic IP UniFi? Correct me if im wrong. I mean, you can search the device, but you can’t logged into it.
hi Nurashid,
Yes you can. Fixed IP packages allocated the same IP to you everytime you connect, while dynamic IP packages give you different IPs when you connect.
But from an external view, IPs are all the same, regardless of whether they belong to fix IP packages or dynamic IP packages.
Regards,
Keith
does the /model/__show_info.php?REQUIRE_FILE=/var/etc/httpasswd work on any other model besides the DLink 1?
Nope only Dlink–but not just the DIR-615, a lot of routers from dlink have this vulnerability
i use the same router and still with Mathopd/1.5p6, and i try to access from outside but not working.
Great , Hw to hack my neighbour password? :/
for me all d-link can be hacked not only 615 but all
Hi BingBang,
Not really. Not all D-Link routers use the same firmware, so not all are susceptible to the flaw.
Check this xiaopan.co
They have forum in chinese and malay too. I have no IT background. But i tried it on my unifi and its really do crack password in 3hrs for 8 digits WPA2. WEP just in couple minutes. Now for my own safety, i keep changing password once a week and use long characters as i can. Wifi also can detect from 2-10km away!! They discus all hacking strategy in that forum. Its our responsibility to keep safe our own network. I’am one of the victims before this and i figure out how to crack.
Thanks Kar2on for sharing this finding. I’m a Unifi user with DIR-615 revision G2, it is very scary that I have affected to the password page exploit for more than 2 years without knowing it.. I have flashed my router to DD-WRT as I found out that there is no way for me to turn off remote access ( at least I cannot find it). I also written down my steps, if anyone interest can have a look. http://cakegiyh.blogspot.com/2014/01/flash-unifi-router-dir-615-g2-to-dd-wrt.html